Dark Web Threat Analysis is a hidden part of the internet that is often associated with illicit activities, cybercrime, and anonymous transactions. While it offers privacy advantages, it is also a hub for cybercriminals engaged in illegal trading, hacking, and financial fraud. Understanding dark web threats is essential for cybersecurity professionals, law enforcement agencies, and businesses looking to protect their digital assets. This article explores the nature of the dark web, the threats it poses, and how organizations can mitigate risks.
Understanding the Dark Web Threat Analysis
1. What Is the Dark Web?
The dark web is a subset of the deep web that is intentionally hidden and requires specialized software such as Tor (The Onion Router) to access. Unlike the surface web, which is indexed by search engines, the dark web operates on encrypted networks, ensuring anonymity for users and site operators.
2. How the Dark Web Works
The dark web relies on decentralized and encrypted communication channels. It uses technologies like Tor and I2P (Invisible Internet Project) to anonymize web traffic, making it difficult to trace activities back to users. Cryptocurrencies such as Bitcoin and Monero are commonly used for transactions, further enhancing anonymity.
3. The Difference Between the Deep Web and the Dark Web
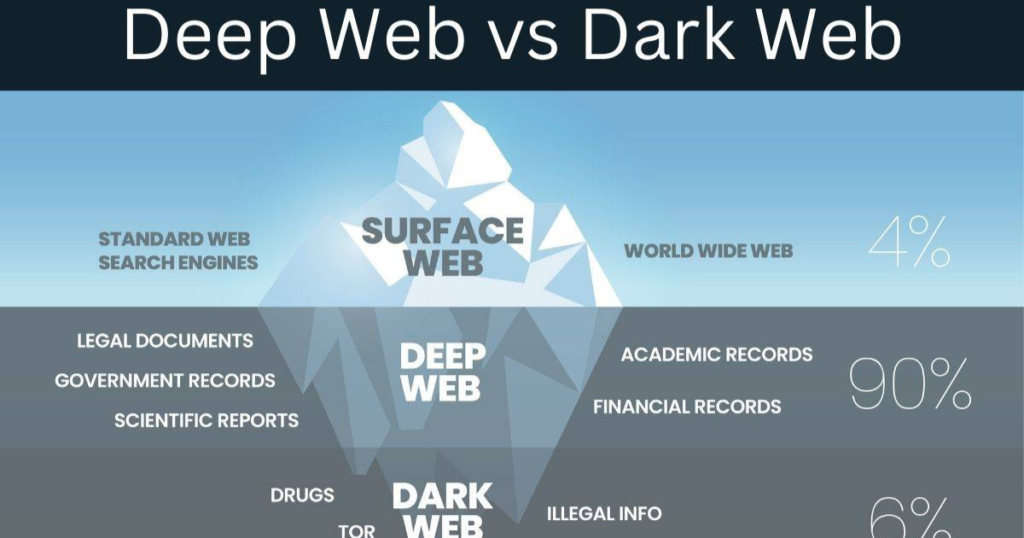
The deep web consists of content that is not indexed by search engines, including private databases, subscription-based services, and internal corporate networks. The dark web, however, is a hidden part of the deep web that is deliberately concealed and often associated with illicit activities.
Cybercriminal Activities on the Dark Web
1. Illicit Marketplaces
Dark web marketplaces facilitate the sale of illegal goods and services, including drugs, weapons, counterfeit documents, and stolen data. These platforms operate similarly to e-commerce sites, with user reviews, escrow services, and cryptocurrency payments.
2. Stolen Data Trading
Cybercriminals buy and sell stolen credentials, credit card information, Social Security numbers, and medical records on the dark web. Data breaches often lead to this information being monetized through underground forums.
3. Hacking Services and Malware
The dark web hosts forums and marketplaces where hackers offer services such as Distributed Denial-of-Service (DDoS) attacks, ransomware deployment, and phishing campaigns. Malware-as-a-Service (MaaS) is also prevalent, enabling non-technical criminals to launch sophisticated cyberattacks.
4. Fraud and Financial Crimes
Financial fraud schemes, including money laundering, fake identity creation, and online scams, are rampant on the dark web. Cybercriminals exploit these platforms to defraud individuals and businesses.
5. Terrorism and Extremist Activities
Extremist groups use the dark web for communication, recruitment, and fundraising. Encrypted messaging services and hidden forums allow these groups to operate beyond the reach of traditional surveillance methods.
Analyzing Dark Web Threats
1. Dark Web Monitoring and Intelligence Gathering
Organizations and cybersecurity firms utilize dark web monitoring tools to track stolen data, emerging threats, and cybercriminal discussions. Intelligence gathered from the dark web helps businesses take proactive security measures.
2. Threat Actors and Their Motives
Dark web threat actors include hackers, organized crime groups, state-sponsored cybercriminals, and hacktivists. Their motives range from financial gain and espionage to ideological activism.
3. Cryptocurrency and Anonymity in Cybercrime
Cryptocurrencies provide a layer of anonymity that facilitates illicit transactions. While Bitcoin is commonly used, privacy-focused coins like Monero and Zcash are gaining popularity among cybercriminals due to their enhanced anonymity features.
Mitigating Dark Web Threats
1. Implementing Strong Cybersecurity Measures

Businesses must enhance their security posture by implementing multi-factor authentication (MFA), encryption, and endpoint security solutions to prevent unauthorized access to sensitive data.
2. Employee Awareness and Training
Many cyber threats originate from human error. Regular cybersecurity awareness training helps employees recognize phishing attempts, social engineering tactics, and other cyber threats.
3. Dark Web Surveillance for Organizations
Enterprises can leverage dark web monitoring services to detect if their sensitive information, such as login credentials or intellectual property, has been compromised. Early detection allows organizations to respond swiftly and mitigate potential damage.
4. Collaboration with Law Enforcement Agencies
Governments and law enforcement agencies continuously monitor dark web activities to identify and apprehend cybercriminals. Organizations should cooperate with these entities to enhance cybersecurity efforts.
5. Blockchain Analysis for Tracking Illicit Transactions
Despite the anonymity of cryptocurrencies, blockchain forensic tools can track suspicious transactions and help identify criminal networks operating on the dark web.
Future Trends in Dark Web Threats
1. Advancements in Encryption and Anonymity
As cybersecurity measures evolve, so do cybercriminal tactics. Future dark web threats may involve more advanced encryption technologies and decentralized platforms that are even harder to monitor.
2. Growth of Ransomware-as-a-Service (RaaS)
Ransomware-as-a-Service (RaaS) is expected to increase, enabling criminals with little technical expertise to launch large-scale ransomware attacks with ease.
3. Increased Use of AI in Cybercrime
Cybercriminals are likely to use artificial intelligence (AI) to automate attacks, bypass security measures, and generate realistic phishing content that is harder to detect.
4. Regulatory and Legal Challenges
Governments and regulatory bodies are working on policies to combat dark web activities. However, legal and jurisdictional challenges make enforcement difficult in many cases.
Also Read: Blockchain Cybersecurity: How Decentralization Is Redefining Digital Security
Conclusion
The dark web remains a significant cybersecurity concern, offering cybercriminals a hidden platform to conduct illegal activities. By understanding the threats posed by the dark web and implementing proactive security measures, organizations can reduce their risk exposure. Ongoing monitoring, collaboration with law enforcement, and advanced cybersecurity strategies are essential in combating dark web threats. As cybercriminal tactics evolve, businesses and security professionals must stay ahead to ensure a safer digital landscape.
FAQs
1. What is the dark web, and why is it a cybersecurity concern?
The dark web is a hidden part of the internet that requires special software to access. It is a cybersecurity concern because it hosts illicit activities such as data breaches, cybercrime services, and financial fraud.
2. How do cybercriminals use the dark web?
Cybercriminals use the dark web to trade stolen data, buy and sell hacking tools, conduct financial fraud, and engage in illegal transactions with anonymity.
3. Can law enforcement track dark web activities?
Yes, law enforcement agencies use advanced tracking techniques, including blockchain analysis and cyber intelligence, to monitor and take down criminal operations on the dark web.
4. How can businesses protect themselves from dark web threats?
Businesses can protect themselves by implementing strong cybersecurity measures, using dark web monitoring services, educating employees on cyber threats, and collaborating with law enforcement agencies.
5. Is the dark web entirely illegal?
No, the dark web is not entirely illegal. It also serves legitimate purposes, such as providing privacy for whistleblowers, journalists, and individuals living under oppressive regimes. However, its anonymity makes it a hotspot for cybercriminal activities.

